Add nix installation script
Currently this will:
- Install nix, if missing
- Prompt user for powerline installation
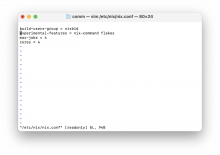
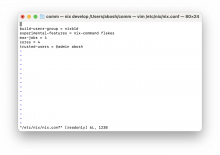
- Configure nix with:
- flakes
- trusted users (for cache)
- Decent job and core defaults
This is implemented with a "reconcilation" configuration model, meaning
the individual actions should be idempotent. Thus safe to run many times.
Depends on D4843