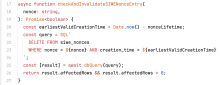
clients signing an ETH message need a recent nonce in the message. they will query the identity service for a nonce, which the identity service will persist, along with its creation time.
we need a new DDB table for the nonces, which we'll provision with terraform.