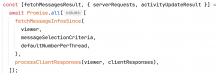
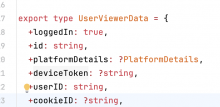
In handleInitialClientSocketMessage we send SIGNED_IDENTITY_KEYS_BLOB request to native or web client if the signed_identity_keys column of the cookies table is missing for an entry with id=cookieID.
These requests will be handled on the client by nativeGetClientResponsesSelector and webGetClientResponsesSelector which will generate functions that return a Promise for an array of ClientClientResponses.
The responses will then be handled by the keyserver with the session-utils:processClientResponses(...) function... which after the next diff will include SignedIdentityKeysBlob from client response in the serverDB cookies table.
Depends on D7050