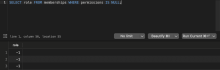
This diff introduces a new thread permission, VOICED_IN_ANNOUNCEMENT_CHANNELS. We also create a propgated/filtered version of this permission, `descendant_toplevel_voiced_in_announcement_channels.
The idea here is that if the user-surfaced VOICED_IN_ANNOUNCEMENT_CHANNELS permission is granted, we give the role both of these permissions. In makePermissionBlob, we can then grant voiced for an announcement thread in a really easy way.
I will be adding a updateRolesAndPermissionsForAllThreads migration once at the end of this entire stack, so that's why I didn't add it here
Addresses ENG-5785
Depends on D9901